Configuring the Server’s TLS Certificates
The system uses TLS server certificates to protect the UI and API end-points
Once installed, the system will be configured with a default SSL certificate issued under a test CA with the subject CN=127.0.0.1
With this certificate in place, you will see warning when accessing via a browser and REST API calls may fail
You may temporarily, install the associated root certificate, located here:
[Install Dir]\config\sslcerts\dbssl_root.cer
into the Local Machines’ Trusted Root Certification Authorities store. This will remove the obvious browser errors. But this is a temporary measure and you should replace this certificate by following the steps below
Create a New SSL Certificate
- Ensure you have a Certificate Issuer configured which includes either an ADCS Template or Local CA Profile that supports SSL/TLS. If one has not yet been configured, refer to the Create a Local Certificate Issuer or Create an ADCS Certificate Issuer guides
- Choose Request > DN Request from the menu
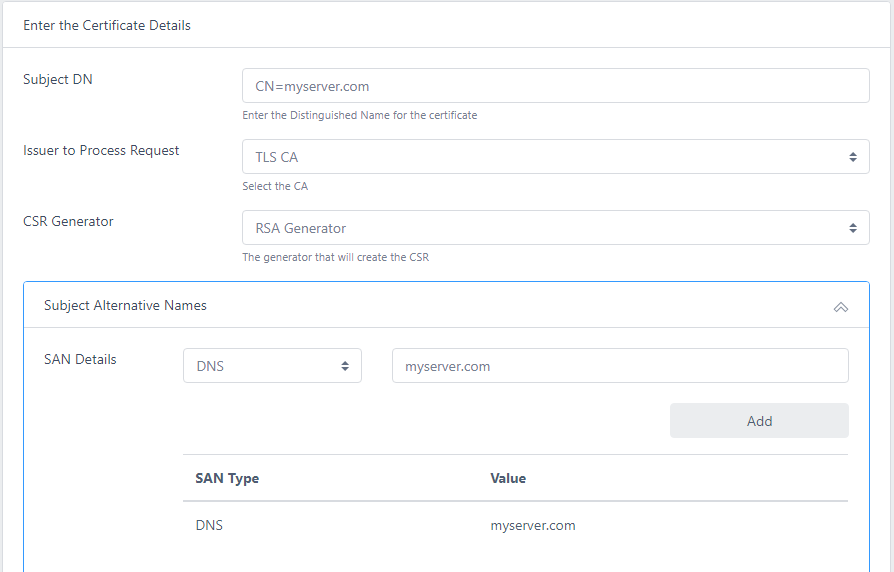
For Subject DN enter the server DNS name as the CN value. E.g. if your server is called myserver.com the DN would contain CN=myserver.com
Choose the Issuer and CSR Generator to process the request
Click on Subject Alternative Names and add a DNS entry that matches the server name e.g. myserver.com
Enter a password and click Request Certificate
When the certificate has been issued, click Download PKCS12 and save the file to .\certdog\config\sslcerts
You can choose any filename and password you like for this certificate. The initial filename is tomcatssl.p12 with a temporary password of temp1234!
If you reuse these values no other updates are required and the new SSL certificate will take effect once you restart the application
If you have chosen a strong password and/or changed the filename, perform the following steps:
- Open
.\certdog\tomcat\conf\server.xml - Locate the following section:
<Connector port="443" address="0.0.0.0" scheme="https" secure="true" SSLEnabled="true" clientAuth="false" sslProtocol="TLS" keystoreFile="C:/certdog/config/sslcerts/tomcatssl.p12" keystorePass="temp1234!" keystoreType="PKCS12"/> - Set keystoreFile to point to your new p12 file and set keystorePass to be the new password
- Save
server.xml - Restart the application